|


Be on the wave or under it™
The News – 10/23/01
|
In
this Issue:
|
Recommended
Reading
|
|
|
I realize this is the only newsletter you’ll ever need,
but if you want more in-depth detail,
|
|
|
check out:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Security
Problems Plague All Operating Systems
Alert SNS
Reader Larry Kuhn (speaking for himself and not his employer) points out that
Microsoft is not the only operating system maker plagued by security problems.
This is certainly true, and is a point I have made repeatedly in the past.
However, it can’t be stressed enough that just because you follow my advice and
don’t expose Microsoft OSes to the Internet, you can’t be complacent. As I
always say, if you’re not terrified about security, you’re not paying
attention.
Larry sent
along a link to an article
written by TechRepublic and published by ZDNet Australia that compares the
raw number of bugs for various operating systems tracked through the Security Focus Bugtraq system. Bugtraq is a
commonly used repository for reports and questions about security bugs. The
TechRepublic article appears to have counted the bug reports for major OSes so
far in 2001 and placed the results in this table:
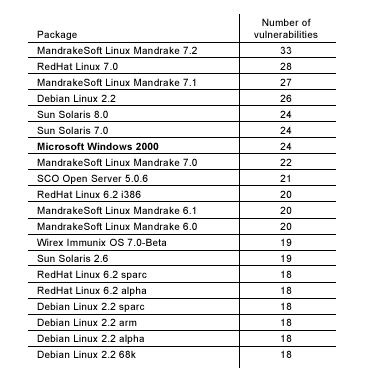
The article
makes the point that Microsoft Windows 2000 at number 7 is far from the most-buggy
OS, and this appears to be true from this analysis. What’s especially
comforting for Microsofties is that last year, Windows NT 4.0 was the bug
champ, with Windows 2000 taking fifth place. Two factors have probably
influenced this better showing: Lots of companies have replaced Windows NT with
Windows 2000, and both platforms have benefited from fixing previously reported
bugs. Windows 2000, for example, is already on Service Pack 2. (A Service Pack
is a compilation of bug fixes that users download and install over an existing
installation. SP-2 is 101MB in size; hardly a quick download.)
Now I’m a
little skeptical of the numbers, and wonder, as did a responder to the article
in TechRepublic's talkback forum, if a raw bug count is really all that
relevant. Of more importance is the amount of time for the vulnerability to get
fixed, the severity of the vulnerability (is it in the wild, or theoretical?), and
the source of the bug report (was it found through a code review or because it
has been actively used to circumvent security?). The poster asserts that closed
source vulnerabilities (like Microsoft’s) are almost always found because
someone has compromised the service, since there is no independent review of the
code as there is in Open Source Software.
Nonetheless,
the results underscore Larry’s point: “People shouldn't feel safer only
because they're using a non-MS OS. I
think that's the only meaningful conclusion that can be drawn from this
article. IMHO, there are non-technical
folks at the CxO level who read stuff like the Gartner recommendation to ditch
IIS and mistakenly come to believe that the same type of risks aren't possible
in the alternative environments.” I couldn’t agree more. Just because you
locked the front door doesn’t mean burglars can’t get in the windows (no pun
intended! ö¿ð ).
Incidentally,
front page news at Security
Focus is a report that a hacker named Beale Screamer has cracked Microsoft’s
Digital Rights Management (DRM) copyright protection scheme which is planned
for use in securing audio files. Another front page article reports that hackers
can get users’ passwords from Cayman Systems' popular 3220-H DSL router. Both
these items underscore the need to not be complaisant or to feel that securing
your computer OS is all you need to worry about.
Larry
continues, once again making a lot of sense: “Security (or the lack of it) is a
multifacted problem - People, Processes and Technology. Any Technologically secure system can be
compromised by an untrained person (someone who sets the "sa" password
to blank), or by well-trained people who don't follow processes (like stickies
on the monitor with passwords written on them, or by not applying security
patches as they become available) that ensure the security of the system.”
Larry points to
an online tool you can use to assess the security of your system, the Microsoft Personal
Security Advisor, written by folks right here in the Twin Cities, Shavlik Technologies, who make an enterprise
version of the tool. The PSA will check the strength of your passwords and see
if you’ve applied all the relevant security patches on your system. I think
everyone in your enterprise should run it and act on its recommendations.
The bottom line
is, as much as I malign Microsoft, they’re by no means the only folks with
security problems. Being the world’s most popular operating system means there
are a lot more crackers out there trying to break their stuff, and that means
their problems are ballyhooed in the press. But, hey, who said being a monopoly
had to be fun? There are advantages to adopting Open Source Software for your Internet-exposed
Web systems. Such systems are supported by fanatical, and I mean really
fanatical, software zealots who consider it a point of pride to find and
eradicate all bugs as quickly as possible. Even if Microsoft, or, heck, even Sun,
for that matter, gets really serious about security, they will be hard pressed
to match the dedication of OSS supporters. If you must use Microsoft software
on the Internet, then you must accept as part of the Total Cost of Ownership
(TCO) the responsibility to constantly update the software with the latest
patches and to be eternally vigilant. In larger enterprises, this obligation
can translate into dedicating one or more employees to the task.
If you’re not
terrified about security, you’re not paying attention.
ZDNet
Australia
Briefly
Noted
- Shameless
Self-Promotion Dept.: I’ve added a security news ticker to the StratVantage
Security Web page. It scrolls up to date information about viruses, worms,
hoaxes and other items of interest regarding computer security. Check it
out.
StratVantage
Security Resources
- Are You Ready for
CRM? I’ve had a
problem with the area known as Customer Relationship Management (CRM) for
some time. It’s a catch-all category for everything from contact
management and sales force automation to call center management, database
marketing, and data mining. Talk to one person about CRM, and they think
you’re talking about contact management software like ACT! or GoldMine.
Talk to another and they think about email marketing. A third person
thinks about call center management. It’s too confusing to lump all these
customer touch areas under one acronym. Often businesses need help in
sorting it all out. Taylor Harkins Group publishes a newsletter that helps
companies make sense of the various issues in CRM, and in their latest
issue they list questions you should ask yourself to assess organizational
readiness before considering a CRM system:
Do you know why your customers buy from you? Can you
find prospective customers just like your current customers?
Can you match your key products and services against
products and services of your competitors? What are the strengths and
weaknesses? Are you selling against them?
Who are future purchasers of your products and
services? What do they look like?
Do you know why your customers are not buying from your
competitors?
Will changes in the economy have and influence your
customer's ability to purchase your products and services? How?
Will changing demographics have an impact on your
business? How?
If your product or service is regulated will pending
changes in legislation affect your profitability? How?
Taylor
Harkins Group
 Wireless Videoconferencing: Tandberg of Norway has announced one of the
first videoconferencing products capable of running on an 802.11b Wireless
LAN (WLAN). The Tandberg 1000 consists of an LCD screen with multiple
network interfaces including IP, ISDN, and WLAN. In wireless mode, you
only need to plug the power cord in the wall, and off you go. Of course,
you’ll have to have a compatible wireless LAN running in your home or
office first. The company envisions folks just grabbing it
and toting it from office to office as the need for videoconferencing
hits. The unit requires a PC/PCMCIA card that fits into the slot at the
top and interfaces with your WLAN. Pricing starts at $5,490. Wireless Videoconferencing: Tandberg of Norway has announced one of the
first videoconferencing products capable of running on an 802.11b Wireless
LAN (WLAN). The Tandberg 1000 consists of an LCD screen with multiple
network interfaces including IP, ISDN, and WLAN. In wireless mode, you
only need to plug the power cord in the wall, and off you go. Of course,
you’ll have to have a compatible wireless LAN running in your home or
office first. The company envisions folks just grabbing it
and toting it from office to office as the need for videoconferencing
hits. The unit requires a PC/PCMCIA card that fits into the slot at the
top and interfaces with your WLAN. Pricing starts at $5,490.
And completely off the subject, who else thinks that looks like Ross Perot
in the picture to the left?
Tandberg- Life in Prison for Hacking? A new bill being considered
in Congress calls for life in prison without a possibility of parole for
people who engage in computer trespass, also known as hackers. The Anti-Terrorism Act,
AKA the ‘‘Uniting and Strengthening America Act’’ or the ‘‘USA Act of
2001’’ has lots of folks up in arms about this provision. The Electronic
Frontier Foundation has publicly condemned the bill for treating
low-level computer intrusion against the government, already a crime under
existing laws, as an act of terrorism. Let’s keep it together, people!
East
Carolinian
- Record Industry Profiteering: As if upping the penalties for
hacking wasn’t enough, our friends at Recording Industry Association of
America (RIAA) tried to glue a self-serving hacking-authorization
amendment onto the Mom & Apple Pie, er, Uniting and Strengthening
America Act. The amendment,
authored by RIAA lobbyists, would have exempted any actions the RIAA would
take to preserve their copyright from the anti-hacking provision. This
means the RIAA would have carte blanche to attack anyone who tried to
circumvent their copyright or Digital Rights Management (DRM) schemes.
That’s pretty extreme, and we can be thankful the amendment was dropped.
Wired
- Cracking
Attacks on Pace to Double: According to Carnegie Mellon University's Computer Emergency
Response Team/Coordination Center (CERT/CC), attacks on Internet computers
should easily double the last year’s reported number. Already, the number
of security incidents reported has reached 34,754, a 60% increase over the 21,756 incidents logged last year. We’re on a pace to see more than 46,000
reported security attacks, more than twice last year’s number.
Newsbytes
 The Sky Is Falling: The FBI appeared to put their foot in it when
they named the file containing the press release warning that Americans
should expect additional terrorist attacks. The two-sentence press release
on FBI.gov said there “may be additional terrorist attacks within the
United States and against U.S. interests overseas over the next several days.”
That’s bad enough, and contributed to the mixed message we’re all hearing
these days: Be aware and worried; act normal or the terrorists will win.
Even more worrisome, however, was the name the FBI chose to give the file
that contained the Web version press release: http://www.fbi.gov/pressrel/pressrel01/skyfall.htm.
Skyfall? As in Chicken Little? Or as in the novel Skyfall from the ‘70s? Or
as in the name of a Transformer, Skyfall the Action Master (pictured)? The
FBI could answer none of these questions, and eventually retitled the
file. Things that make you go “Hmmmmmm.” The Sky Is Falling: The FBI appeared to put their foot in it when
they named the file containing the press release warning that Americans
should expect additional terrorist attacks. The two-sentence press release
on FBI.gov said there “may be additional terrorist attacks within the
United States and against U.S. interests overseas over the next several days.”
That’s bad enough, and contributed to the mixed message we’re all hearing
these days: Be aware and worried; act normal or the terrorists will win.
Even more worrisome, however, was the name the FBI chose to give the file
that contained the Web version press release: http://www.fbi.gov/pressrel/pressrel01/skyfall.htm.
Skyfall? As in Chicken Little? Or as in the novel Skyfall from the ‘70s? Or
as in the name of a Transformer, Skyfall the Action Master (pictured)? The
FBI could answer none of these questions, and eventually retitled the
file. Things that make you go “Hmmmmmm.”
- A Sound Link: US Robotics has released a cool gadget
that sets up a wireless connection of up to 1,000 feet between your
computer and stereo. So if you’re tired of listening to your MP3s
(lawfully ripped from your own, fully licenced CDs, of course) on your
dinky computer speakers, this $100 toy’s for you.
US
Robotics
Return
to Mike’s Take
|